Ok, I shouldn’t say my first Android app. It’s my first published Android app. Binary Clock is simply an app that displays a binary clock in either BCD or True Binary mode. Learn how to read a binary clock on Wikipedia.
Â
Â
Ok, I shouldn’t say my first Android app. It’s my first published Android app. Binary Clock is simply an app that displays a binary clock in either BCD or True Binary mode. Learn how to read a binary clock on Wikipedia.
Â
Â
If you have Vonage Mobile on your Android based smartphone you know that you’re able to make free calls over WiFi. I’m currently in a different country using a satellite Internet connection and the Vonage Mobile app is having trouble staying connected to the WiFi here, so I’m using 3CXPhone setup with the SIP server information for Vonage Mobile which is working much better (I tried using fring, but people I called couldn’t hear me although I could hear them). Here are two methods on how to find your SIP information for Vonage Mobile so that you can use other devices or other Android apps with SIP capabilities.
Using ADB
Using a terminal emulator on your Android (like Better Terminal Emulator) for rooted phones ONLY:
Â
|
Vonage Mobile for Android |
3CXPhone for Android (VoIP) |
fring |
Better Terminal Emulator Pro |
|
|
|
|
|
I’m standing at the ruins of an old roof top elementary school on planet Crest Prime, the year is 4793E. I’ve travelled 42 million light yearsE (~31.6 million light yearsCP) to visit this once mega city, Cristal, on the sixtieth anniversary of The Bang. The Bang, as it’s called, was a double solar flare, ejected simultaneously from each of the planets two suns. I remember the day six decades ago when the 12 billion people inhabiting this planet were nearly wiped out. I can feel the wind on top of the 180 story building just as it was that day. I jumped off my favorite swing and stood watching as the air shuttle fell from the sky coming straight at us. I remember an urgent sense of fear rushing throughout my body knowing there is nothing I can do to stop it. The shuttle is on an out of control approach, its pulsed terrestrial jet engines curiously quiet, just over the top of the spaceway which runs dangerously close to the elementary school, too close for any parents’ comfort. And then it happens. The shuttle smashes into the spaceway ripping it to shreds as pieces go flying all over the schoolyard. Children are running with nowhere to go, nowhere to escape the carnage. The shuttle slams into the rooftop and comes to a screeching halt, engulfed in fire. The schoolyard is destroyed, my friends lie motionless. I’m all alone.
   Â
Tanner Jepsen
Professor Alexander Vaughan Ames
English Composition I
July 12, 2010
Assignment 4.4: The Travelling Salesman Problem
The Travelling Salesman Problem is a complex problem in Computer Science, however developing a computer algorithm to overcome the problem in the most efficient way possible is not an unmanageable or difficult task. The problem states that given a list of cities and the distances between each pair of cities, finding the shortest possible route that visits each city only once is computationally difficult. For Humans, you might say this is an easy problem. Just look at a map and visually find the shortest route. For computers, it is a far more complex problem. Imagine that the list of cities includes hundreds, thousands or even tens of thousands of destinations spread across a large geographical area. Perhaps it’s not cities at all, but countries or a list of coordinates. In the future it may even be planets, solar systems, galaxies etcetera. The problem can quickly become far too much for a Human to solve. Even for a computer, as the list grows larger it will take the computer longer and require more resources to find an efficient solution. The makers of a popular space game, Eve-Online by CCP, graciously make their entire game database available to the public which is perfect for exploring this problem.
The Eve-Online universe includes 5431 solar systems spread across 1109 constellations and 97 regions. The only way to travel between solar systems is by using jump gates that propel a space ship to faster than light speeds. Attempting to travel between solar systems without a jump gate would take several lifetimes and is simply unfeasible and so using the jump gates is considered to be a constraint. Constraints are a good thing because they limit the number of options the computer can take to travel, which means less for the computer to look at. Finding the quickest route between two solar systems is a fairly simple process using a breadth first search. That is, starting from solar system “A”, check to see if any of the connected solar systems is the final destination. If not, do the same thing with each connected solar system and continue the process until the destination solar system “B” is found. Throughout the process, the computer algorithm needs to keep track of where it has already been so that it doesn’t visit the same place twice. Depending on how many solar systems need to be travelled through to get to the destination, this search algorithm, although extremely simple, could take a very long time to find the destination and requires large amounts of computer memory to keep track of the solar systems that were already visited. There are a few heuristic measures that can be taken to minimize the amount of time it takes and the amount of memory required to find the quickest route.
The Eve-Online database does not directly provide the distance between two solar systems. It does, however, provide the x, y and z coordinates in 3D space of where all the solar systems lie. Using the x, y and z coordinates of two solar systems we can use Pythagorean’s Theorem to determine the distance between them which, in effect, is another constraint. Pythagorean’s Theorem states that the length of a hypotenuse on a right triangle is equal to the square root of the length of the adjacent squared plus the length of the opposite squared, or c = sqrt(a2 + b2). We can further this in 3D space so that the distance between two solar systems would be calculated thusly:
The original algorithm can now be modified to take into account the distance calculated between two solar systems. The algorithm can be programmed so that it does not travel through a solar system that takes it further away from the destination unless all other options have been exhausted. Although this is great, and the computer is finding the route faster, there is still more that can be done.
As previously explained, the Eve-Online database places each solar system into constellations and regions, just as cities are placed into counties and states. As the algorithm travels between solar systems it will cross constellational and regional boundaries, just as in real life, when a person travels between cities he will cross county and state lines to get to his destination. This is another constraint. Before finding the route between solar system “A” and solar system “B”, the algorithm can find the route between the constellations that each solar system lies within. Once it has the route between constellations “A” and “B”, the algorithm can then eliminate adjacent solar systems from the search path by determining if said solar system lies within one of the constellations that have already been found to be along the route. If it doesn’t, the solar system is ignored, potentially removing a very large chunk of search paths from the search algorithm. The same concept can be implemented for regions as well, however depending on the size of the universe, as in the Eve-Online example, it may not be beneficial.
At this point the algorithm is very fast and can be used in a production environment, but there are other constraints that can be added as a convenience to the user. The database includes a security status for each solar system. On a scale from 0.00, indicating no security, to 1.00, indicating complete security, this constraint can be added to the search algorithm so that the user may avoid low security solar systems, thereby avoiding pirates and certain death if the proper arrangements are not made to travel with a skilled security detail.
Exploring the Eve-Online game universe it has been found that the travelling salesman problem is not an unmanageable problem at all on today’s powerful computers. At the hands of a skillful computer programmer, using constraints to her advantage it is possible to minimize the amount of required processor and memory resources to quickly find a solution to the most common routing problems. Many search algorithms are in use today, perhaps some can be made more efficient, reducing operating costs for businesses such as UPS, FedEx, USPS, and DHL to the local courier service, airport shuttle service, and even the pizza delivery man.
CCP. “Eve Online | Data Export.” 1997-2007. Eve Online. 2010 <http://www.eveonline.com/community/toolkit.asp>.
Wikimedia Foundation, Inc. “Pythagorean theorem.” 8 July 2010. Wikipedia. 12 July 2010 <http://en.wikipedia.org/wiki/Pythagorean_theorem>.
—. “Travelling salesman problem.” 10 July 2010. Wikipedia. 12 July 2010 <http://en.wikipedia.org/wiki/Travelling_Salesman_Problem>.
http://code.google.com/p/exfat/
sudo apt-get install subversion scons libfuse-dev gcc
cd ~
svn co http://exfat.googlecode.com/svn/trunk/ exfat-read-only
cd exfat-read-only
scons
sudo scons install
cd ..
rm -rf exfat-read-only
sudo mkdir [mountpoint]
sudo mount -t exfat-fuse [device_path] [mountpoint]
Replace [device_path] with the device path to your exfat partition, for example: /dev/sdb1. Replace [mountpoint] with the path to your mount point, for example: /media/disk
C:\>openssl s_client -crlf -connect imap.gmail.com:993
CONNECTED(00000003)
depth=1 /C=US/O=Google Inc/CN=Google Internet Authority
verify error:num=20:unable to get local issuer certificate
verify return:0
---
Certificate chain
0 s:/C=US/ST=California/L=Mountain View/O=Google Inc/CN=imap.gmail.com
i:/C=US/O=Google Inc/CN=Google Internet Authority
1 s:/C=US/O=Google Inc/CN=Google Internet Authority
i:/C=US/O=Equifax/OU=Equifax Secure Certificate Authority
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIDWzCCAsSgAwIBAgIKYgnCCAADAAAJ5DANBgkqhkiG9w0BAQUFADBGMQswCQYD
VQQGEwJVUzETMBEGA1UEChMKR29vZ2xlIEluYzEiMCAGA1UEAxMZR29vZ2xlIElu
dGVybmV0IEF1dGhvcml0eTAeFw0wOTA3MTcxNzEzNDFaFw0xMDA3MTcxNzIzNDFa
MGgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMRYwFAYDVQQHEw1N
b3VudGFpbiBWaWV3MRMwEQYDVQQKEwpHb29nbGUgSW5jMRcwFQYDVQQDEw5pbWFw
LmdtYWlsLmNvbTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA+O0vc2pslfjk
pbxnBF4iznJMrP9Qi3fHjKqA3P2RynTcbnZfGEGMKcPeXHT4IOH6XUnf+4Jw+z7I
KiMtjX8IVGo7DeXec/ZREasEZnpMGisxN7+qk7Ho6HyaglQTAFIQJP99UFJkHO9x
dGDy5d2j9senPad1BqtyaIRGkJpHizUCAwEAAaOCASwwggEoMB0GA1UdDgQWBBT0
WHOeLKf4+VNADzHzGh+AEV+6fjAfBgNVHSMEGDAWgBS/wDDr9UMRPme6npH7/Gra
42sSJDBbBgNVHR8EVDBSMFCgTqBMhkpodHRwOi8vd3d3LmdzdGF0aWMuY29tL0dv
b2dsZUludGVybmV0QXV0aG9yaXR5L0dvb2dsZUludGVybmV0QXV0aG9yaXR5LmNy
bDBmBggrBgEFBQcBAQRaMFgwVgYIKwYBBQUHMAKGSmh0dHA6Ly93d3cuZ3N0YXRp
Yy5jb20vR29vZ2xlSW50ZXJuZXRBdXRob3JpdHkvR29vZ2xlSW50ZXJuZXRBdXRo
b3JpdHkuY3J0MCEGCSsGAQQBgjcUAgQUHhIAVwBlAGIAUwBlAHIAdgBlAHIwDQYJ
KoZIhvcNAQEFBQADgYEAXLvdKJJ6ivWAi29p4pPo4cirMEYnRlpNOmPVAW4QYcSq
lEZhm4cQdyitFo9cxiwNgbBjJk8O+oiOhnueT44RXotEE7j3KnNyPRRZg0OCagGC
4G71fFA11P1L0fSd/7k52/DbZQBea3tJgkseoGL50UVvnJm+LZOovIGxoQzipJk=
-----END CERTIFICATE-----
subject=/C=US/ST=California/L=Mountain View/O=Google Inc/CN=imap.gmail.com
issuer=/C=US/O=Google Inc/CN=Google Internet Authority
---
No client certificate CA names sent
---
SSL handshake has read 1704 bytes and written 300 bytes
---
New, TLSv1/SSLv3, Cipher is RC4-MD5
Server public key is 1024 bit
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1
Cipher : RC4-MD5
Session-ID: 059F9016BB7EF76FC1080A02368D4812EF5619D9176C176412A0A8F786C2E71C
Session-ID-ctx:
Master-Key: EFE3B0BFEAE372829EA6B9B306BEB5BE2F5BBE5D325CF9F01940BB25C8353A16
08DA3A85DC0D4581DD482F2C7B9759EB
Key-Arg : None
Start Time: 1264807587
Timeout : 300 (sec)
Verify return code: 20 (unable to get local issuer certificate)
---
* OK Gimap ready for requests from 71.231.242.11 31if8927301pzk.40
A01 LOGIN username password
* CAPABILITY IMAP4rev1 UNSELECT LITERAL+ IDLE NAMESPACE QUOTA ID XLIST CHILDREN
X-GM-EXT-1 UIDPLUS COMPRESS=DEFLATE
A01 OK username authenticated (Success)
A02 SELECT INBOX
* FLAGS (\Answered \Flagged \Draft \Deleted \Seen)
* OK [PERMANENTFLAGS (\Answered \Flagged \Draft \Deleted \Seen \*)]
* OK [UIDVALIDITY 2]
* 2636 EXISTS
* 0 RECENT
* OK [UIDNEXT 15043]
A02 OK [READ-WRITE] INBOX selected. (Success)
A04 IDLE
+ idling
DONE
A04 OK IDLE terminated (Success)
A05 LOGOUT
* BYE LOGOUT Requested
A05 OK 73 good day (Success)
read:errno=0
A few years ago I was asked to help someone create a color wheel using Photoshop. With this project I learned a lot about color theory and computationally converting from RGB to HSV and vice versa. I decided to post the color wheel here for my own future reference.
And here’s the PSD file.
Recently at work we had to need to convert XLSX files to XLS files in bulk. My boss discovered that having to convert many files individually is not a fun process so I wrote this little program to automate the process. Here’s a screen shot:
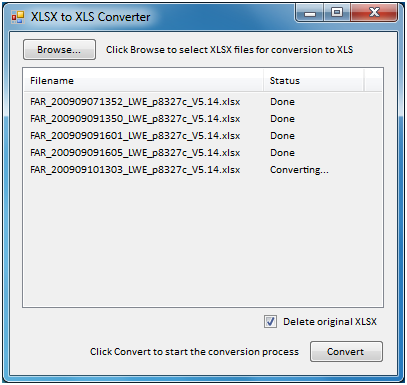
Click here to download the program. It requires that you have Microsoft Office 2007 or newer installed and the Microsoft .Net Framework 3.5.
Earlier this week I was on a mission to convert an NRG image file to an ISO image file. I didn’t want to download a program that someone had already written like nrg2iso and instead preferred to use something like the linux dd command or write my own program that could do. I started digging into the NRG file format and found that it’s actually an IFF file. The documentation on how Nero implemented the IFF format into their NRG files isn’t very clear at all and is incorrect so with the information I was able to find I had to reverse engineer the format myself. Here’s how to convert an NRG image to ISO using the dd command (if you’re on windows you can install Cygwin to gain access to the dd command).
An NRG image is a CD-ROM image followed by Nero’s “footer” about the image, it’s cue sheets, cd text, and so on. The last twelve bytes of an NRG image file contain the NER5 header and an offset to the first CUE sheet of the image. Even though this offset is just a pointer to the first CUE sheet, you can use it determine the actual length of the image. Here’s what to do with dd.
That’s it.. now mount your ISO image to a virtual cd/dvd/bd drive like Virtual CloneDrive (or burn it) and make sure it works before deleting your NRG file.
I just got back from CRC again, this time for Afghanistan. If you haven’t read my previous post for when I went to Iraq you can read it here: https://www.tannerjepsen.com/?p=59. Very little has changed since the last time I went. Now if you need shots they send you off post to a clinic where you’ll have to pay to get your shots. This only applies to contractors who are not on active duty (all of us?), aren’t retired, and aren’t a military dependents.
This time I stayed in the barracks and did not have my own rental car. I was with six other people and we all shared a 12 pac van. I was also TDY and return (not taking a SAAM flight overseas/the unit we’re supporting is providing transportation).
As far as training goes, this time I did do ALL of the training before getting to CRC. If you have an AKO account, you can find SERE training here: https://jkolms.jfcom.mil/. The course title is “SERE 100 Code of Conduct Training Course.”
That’s pretty much it. Again, I highly recommend reading my previous post here: https://www.tannerjepsen.com/?p=59.